Simplifying Access with Multiple Identity Providers in ServiceNow
By Kyle Commette
In today’s digital landscape, managing access across multiple platforms and services is critical for organizations of all sizes. To streamline authentication and ensure secure access, many businesses are adopting multiple Identity Providers (IdPs). ServiceNow, being a robust platform, offers excellent support for integrating multiple IdPs, including OpenID Connect (OIDC) and Security Assertion Markup Language (SAML), to deliver seamless user experiences while maintaining strong security protocols.
In this post, we'll explore how ServiceNow enables the configuration of multiple IdPs, discuss best practices for incorporating both OIDC and SAML, and demonstrate how to provide a user-friendly login experience with these technologies.
Why Use Multiple Identity Providers?
Many organizations require multiple IdPs to serve various user groups. For instance, employees may use OIDC for internal systems, while external contractors or partners use SAML. ServiceNow’s ability to support multiple IdPs allows businesses to:
Flexibly Authenticate Different User Groups: Employees, partners, and contractors can use their preferred authentication methods without compromising security.
Enhance Security: By supporting Multi-Factor Authentication (MFA) through different IdPs, organizations can protect sensitive resources across internal and external users.
Simplify Access Management: ServiceNow ensures seamless authentication across platforms by integrating multiple IdPs into a unified system, reducing the complexity of user access.
Configuring Multiple Identity Providers in ServiceNow
ServiceNow allows administrators to configure both OIDC and SAML IdPs within the same instance, enabling flexibility in how users authenticate. Here’s a step-by-step guide on configuring multiple IdPs:
Install plugin “Integration – Multiple Provider Single Sign-On Installer”
Plugin id: com.snc.integration.sso.multi.installer
Enable single sign on for the ServiceNow instance
Navigate to Multi-Provider SSO > Administration > Properties
i. Enable Account Recovery User
ii. Enable multiple provider SSO = True
iii. Enable auto import of users from all identity providers into the user table = True
iv. Enable debug logging for the multiple provider SSO integration = True
Add the Identity Providers (IdPs):
Go to Multi-Provider SSO > Identity Providers.
Click on New and select the appropriate protocol, either OIDC or SAML.
Configure OIDC Provider:
Configure OpenID connect based SSO automatically by importing the well- known configuration URL. Required for importing:
Name, Client ID, Client Secret, Well Known Configuration URL
Alternatively, the form can be manually configured.
Configure SAML Provider:
ForSAML, upload the Metadata XML provided by the SAM LIdP, or manually configure fields like Entity ID and Identity Provider URL.
Ensure that the correct Assertion Consumer Service (ACS) URL is specified to enable the response to be handled correctly in ServiceNow. Example of Microsoft Entra Enterprise App for SAML
Example of Microsoft Entra Enterprise App for SAML
ServiceNow record to create SAML IdP connection
Test Connectivity:
Once your configurations are complete, test each identity provider to ensure users can authenticate successfully.
Delivering a User-Friendly Login Experience
While it’s essential to offer multiple authentication options, ensuring that the user experience remains intuitive is equally important. Here’s how to create a user-friendly login experience when configuring multiple IdPs in ServiceNow:
1. Customizing the Login Page
ServiceNow allows you to copy the portal login page and login widget to present users with an experience that fits your users' expectations. In this case, display buttons for OIDC and SAML authentication, with clear labels such as:
"Employee Login” (OIDC)
"Partner Login” (SAML)
Ensure that the login buttons are visually distinct and easy to find. Here’s an example of how you can organize the login options on the page:
Selecting an option will initiate the appropriate SSO. The screenshot below represents SAML using Microsoft Entra Enterprise App for ServiceNow:
2. Simplifying User Flow
With multiple IdPs in place, it’s crucial to set up routing to ensure the different user types have consistent landing page experience. Example would be routing ITIL agents to the ServiceNow Homepage and all other users to the Employee Center Portal.
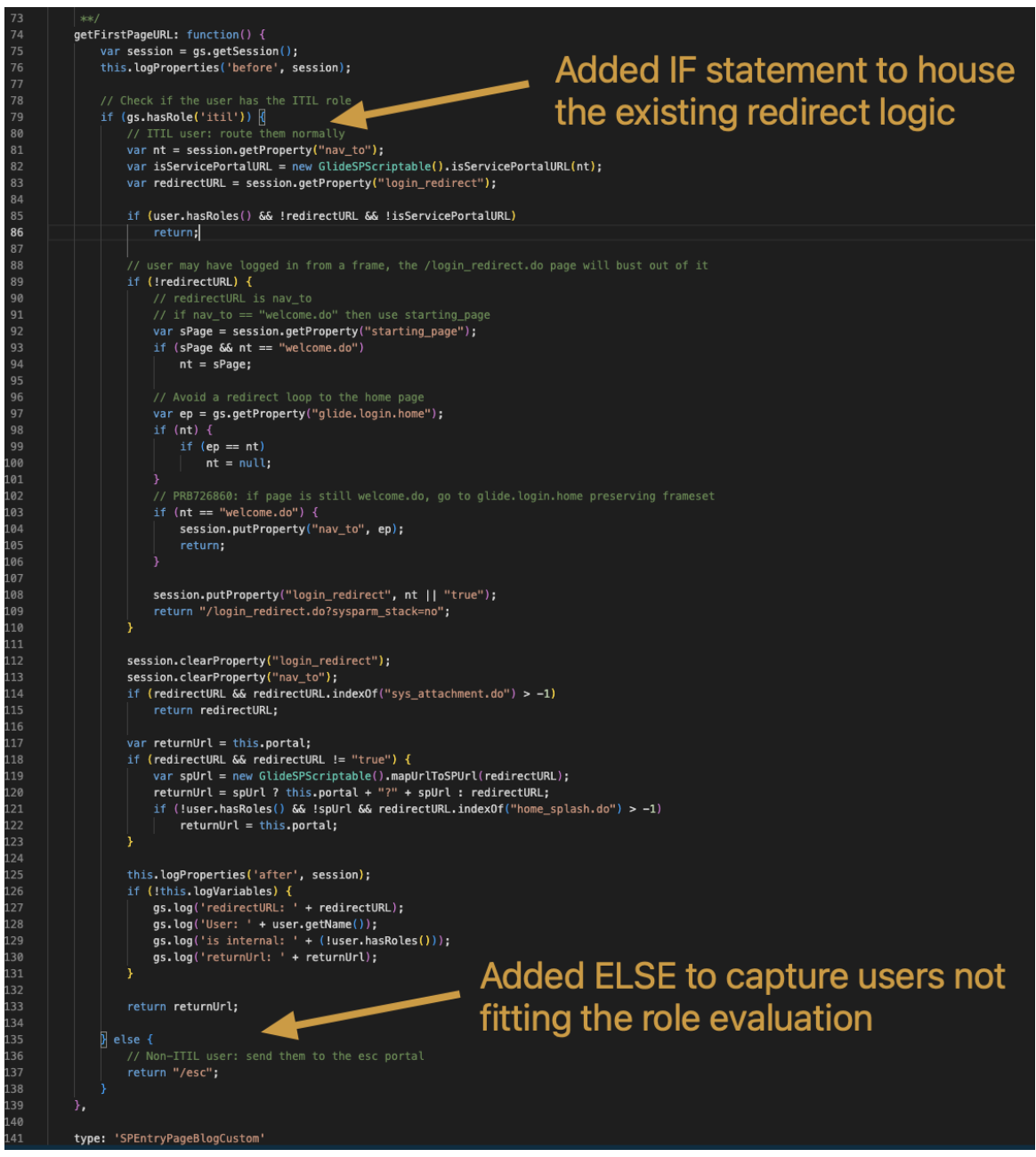
Configure the SPEntryPage Script to redirect users based on roles
To accomplish this, Navigate to System Definitions > Script Includes
Find and click into the record SPEntryPage. Rename it and Insert and Stay.
Looking at the record’s script we have two important functions.
getLoginURL();
i. Defines if the user routes to the backend sign in page or portal sign in page. This will get us to our custom login page.
getFirstPageURL();
i. Handles the routing logic after the user successfully logs into the instance.
No modification is needed to getLoginURL(). For the redirect we will focus the
added logic to getFirstPageURL().
On the new record, the code below can be added to the script.
On line 79:
On line135 add:
Once the configurations have been changed. We need to modify two system properties to activate the logic coming from the copied SPEntryPage script.
Navigate to the ServiceNow system properties. Add the appropriate value to each of the two properties.
Property:glide.entry.page.script
Value:newSPEntryPage().getLoginURL();Property:glide.entry.first.page.script
Value:newSPEntryPage().getFirstPageURL();
NOTE: Please check that the values you add to the properties correspond with the copied SPEntryPageCopy record name. When copying, the SPEntyPage name will change. Example:
• Value: new SPEntryPageCopy().getFirstPageURL();
By configuring these rules, ServiceNow can automatically direct users to the appropriate IdP, ensuring a seamless experience while maintaining security. Below is the expected redirection for each persona in our example:
Fulfiller Users (ITIL role)
External Users (roles other than ITIL)
Enhancing Security with MFA Integration
Security is a major concern when working with multiple identity providers. Integrating Multi-Factor Authentication (MFA) with both OIDC and SAML further strengthens access control.
OIDC MFA:
Most OIDC providers, like Azure AD or Google Identity, support MFA out of the box. Ensure that MFA is enabled within the OIDC provider’s settings and that ServiceNow supports the secondary authentication method.SAML MFA:
SAML IdPs often provide MFA options as well.You can configure these within the SAML provider’s dashboard and enforce MFA based on user roles or conditions like access to sensitive data.
Best Practices for Multi-IdP Management in ServiceNow
Regularly Review Configuration: Ensure that both IdP configurations are reviewed periodically to keep certificates, keys, and URLs up to date.
Test Authentication Regularly: Test authentication from both internal and external user perspectives to catch any issues before they impact users.
Monitor Logs for Errors: Use ServiceNow’s SAML and OIDC debugging to monitor logs for issues such as authentication failures, expired certificates, or signature verification errors.
Ensure a local login user is defined in Production. It is essential that one user can access the instance in case SSO stops working. Tagging the local login user with the ACR role will limit this user's ability to do Admin functions to solely the Multi-Provider SSO module. Keeping strong security around Admin privileged users.
Having a local login user is also preferred to ensure access remains available if an issue arises on the sub-production instance during a clone from production.
If proper cloning exceptions are not put in place to exclude certain tables from being cloned (e.g., users and identity providers), it is possible that the clone could override the sub-production SSO configurations with those from the production instance, potentially causing conflicts with the setup on the Identity Provider's side.
Wrapping Up
Managing multiple identity providers in ServiceNow can greatly enhance both the user experience and security. By supporting OIDC and SAML, organizations can ensure that all user groups have a seamless and secure way to access the platform. With the right configurations and best practices in place, ServiceNow becomes a central hub for identity management across all services.
If you’re looking to implement multiple IdPs in your ServiceNow instance, or have any questions about optimizing your identity management, feel free to reach out to esolutionsONE!
By following these steps, you can simplify access management with multiple IdPs, deliver a smooth user experience, and maintain strong security protocols across your ServiceNow environment.












